Web
Web50
检查js代码,复制出来,把clicks=0直接改成var clicks=108000,然后整个粘贴到控制台中,回车
flag:moctf{Here_Is_Your_Surprise}
其他Web
Web被欺负得好惨,完美避开了所有窝会的东西……QAQ
RE
只有Android部分
re150 我的VIP(Android)
感谢@Sakura师傅
jadx打开,定位到MainActivity:
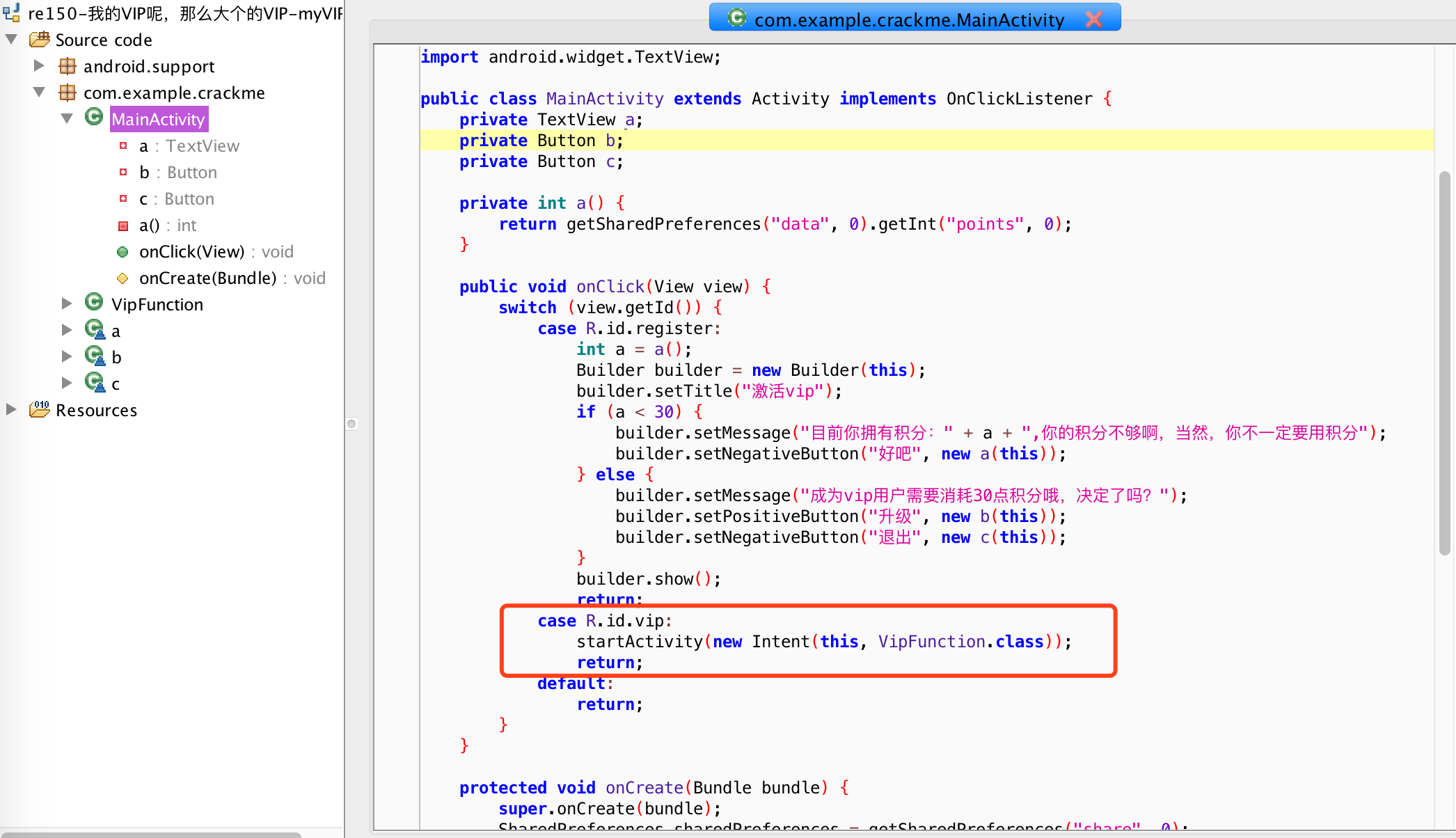
跟过去:
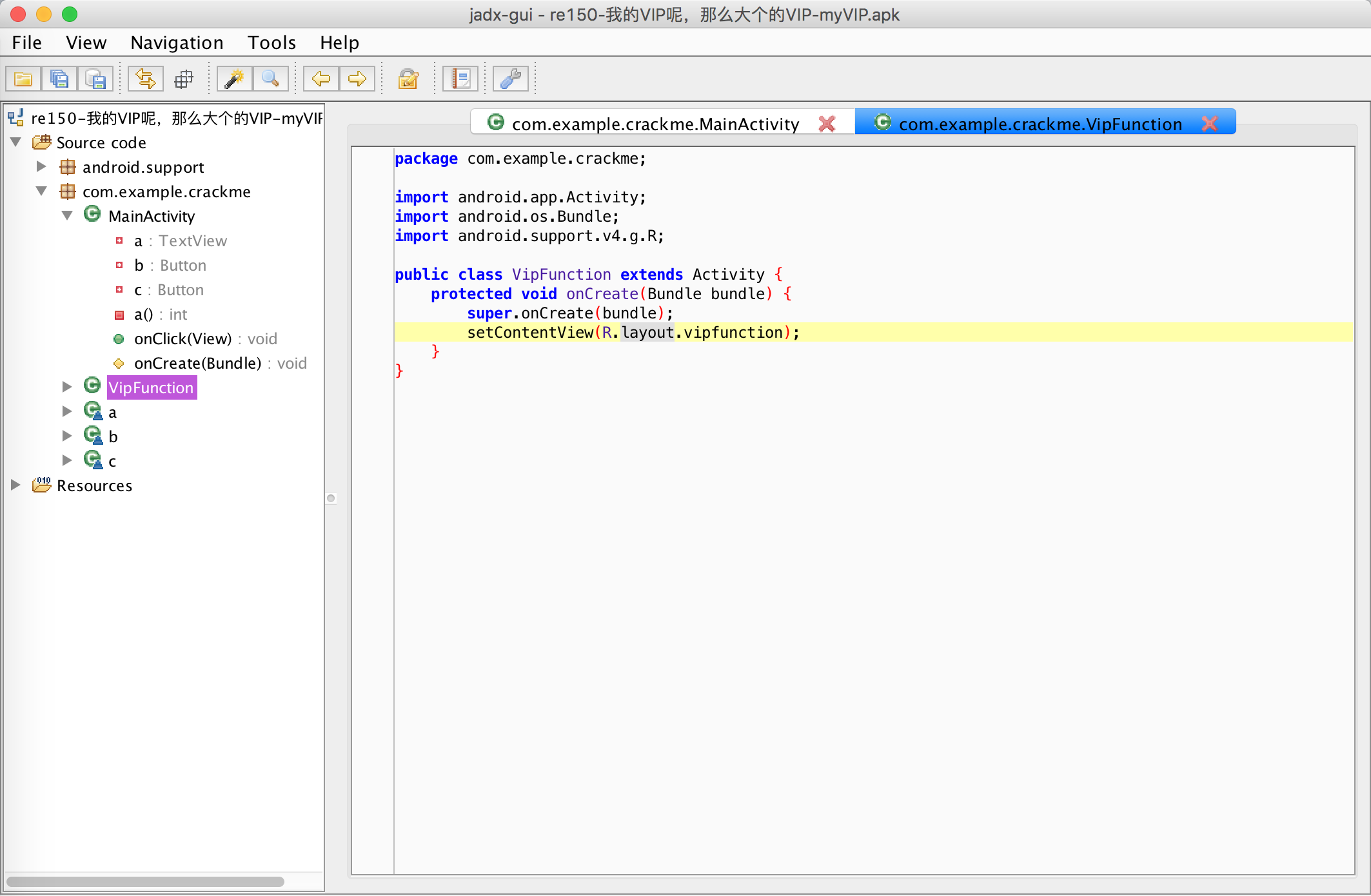
找到:
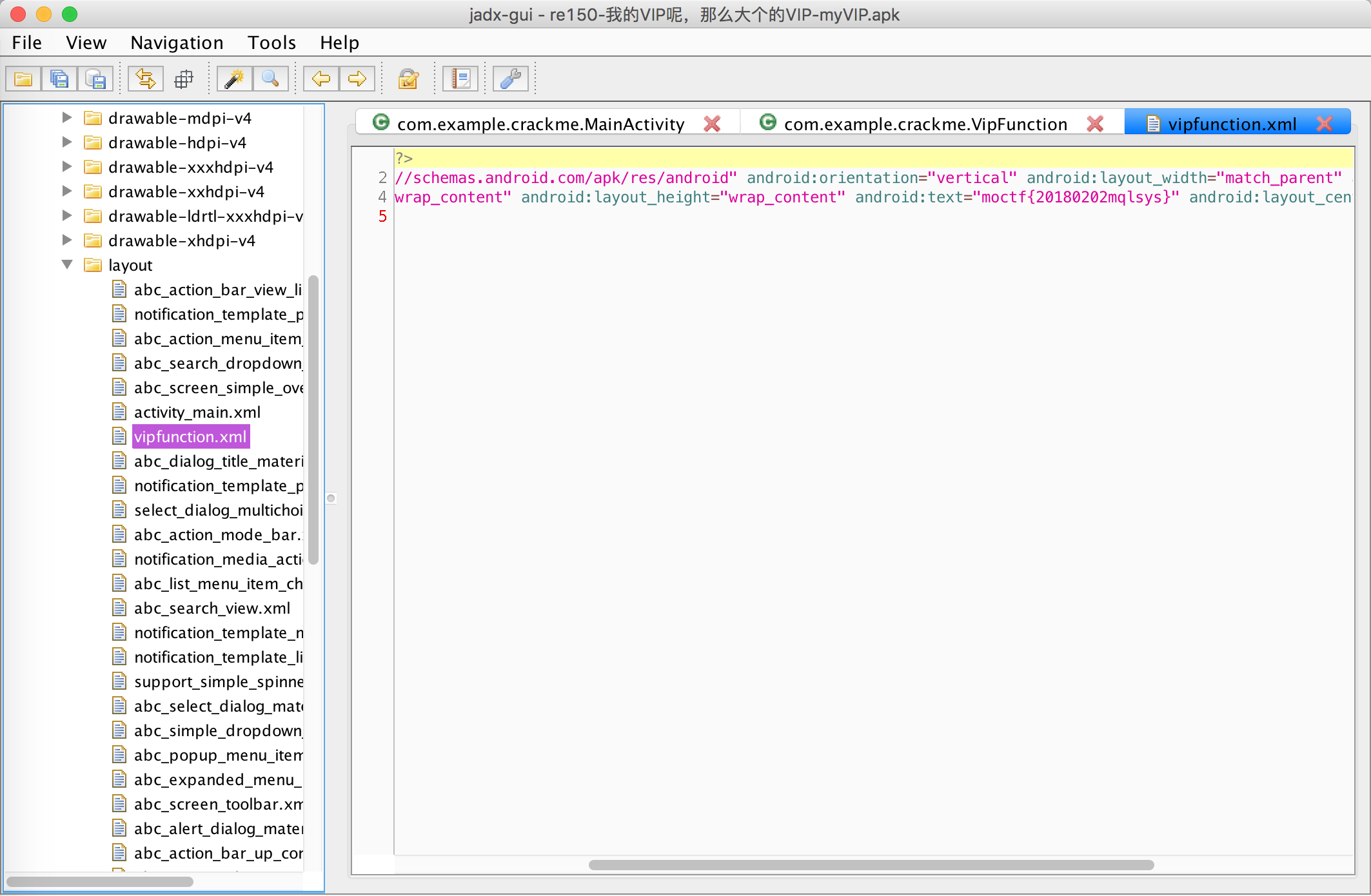
flag:moctf{20180202mqlsys}
re200 哇,有毒吧(Android)
jadx打开,定位到MainActivity:
|
|
|
|
第一个base64解码,真的有毒
|
|
Misc
流量分析
选中Data字段,应用为列,竖着读:
|
|
base全家桶
|
|
颜文字
控制台执行
moctf{Yan_Wen_Zi}
奇怪的十六进制
|
|
|
|
|
|
先越过这道栅栏再说
|
|
空word
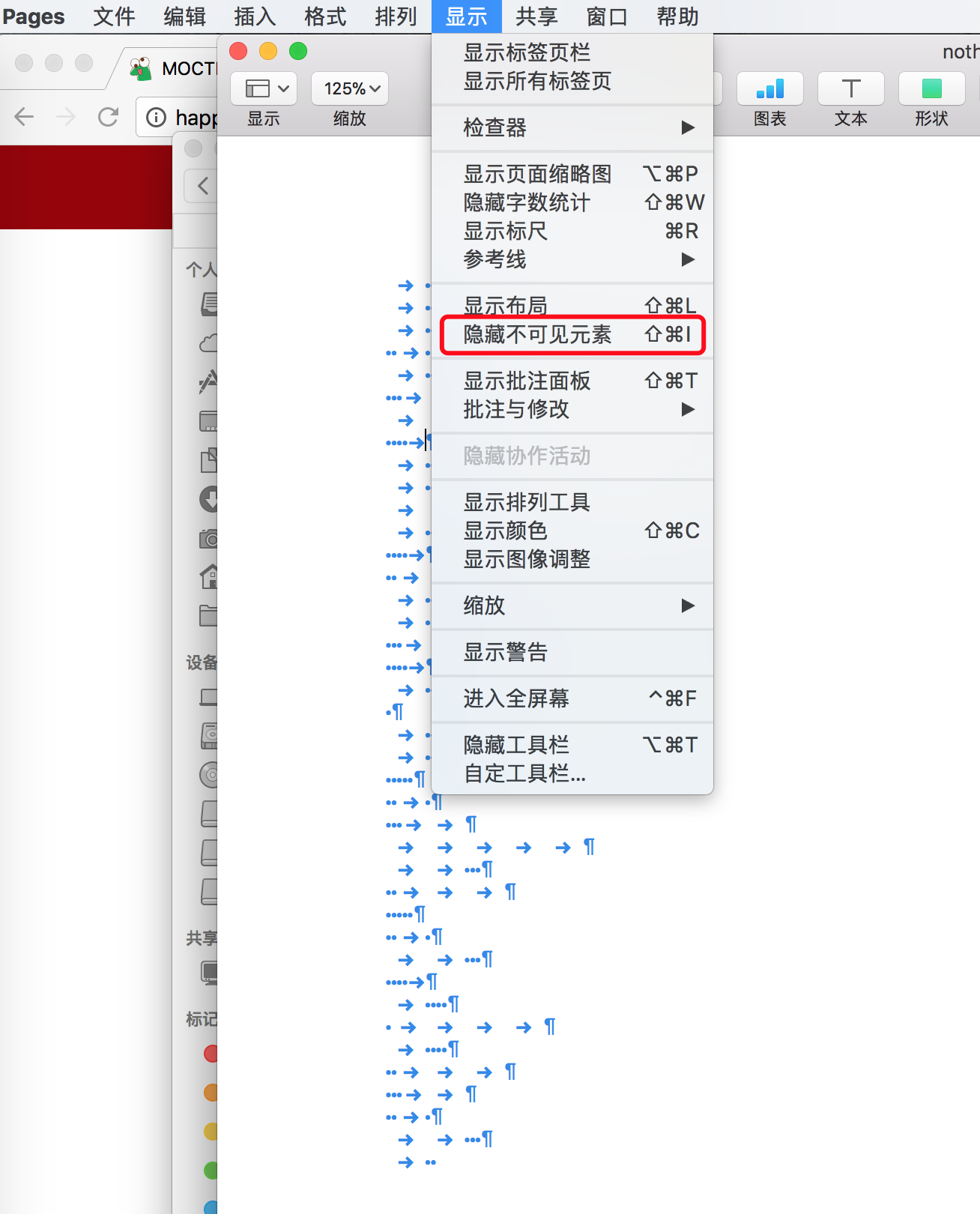
显示不可见元素,·当成.,箭头当成-,一行一个,转换为摩斯密码:
|
|
摩斯解密:
|
|
|
|
一万年的爱有多久
感谢@pcat师傅
解题思路就是写个脚本来解压题目的zip文件(Mac下窝试了一下,归档工具会自动循环解压,但是速度好慢)
pcat师傅的脚本(py2):
|
|
照着pcat师傅的脚本,自己写了一个试试,代码如下(py3):
|
|
解压得到flag,直接打开就可以看到flag啦
flag:moctf{Just_a_few_minutes}
是兄弟就来干我
感谢@pcat师傅,@一叶飘零师傅
flag.zip要密码,那密码就从tanwanlanyue.png里找
binwalk没结果,Stegsolve打开:
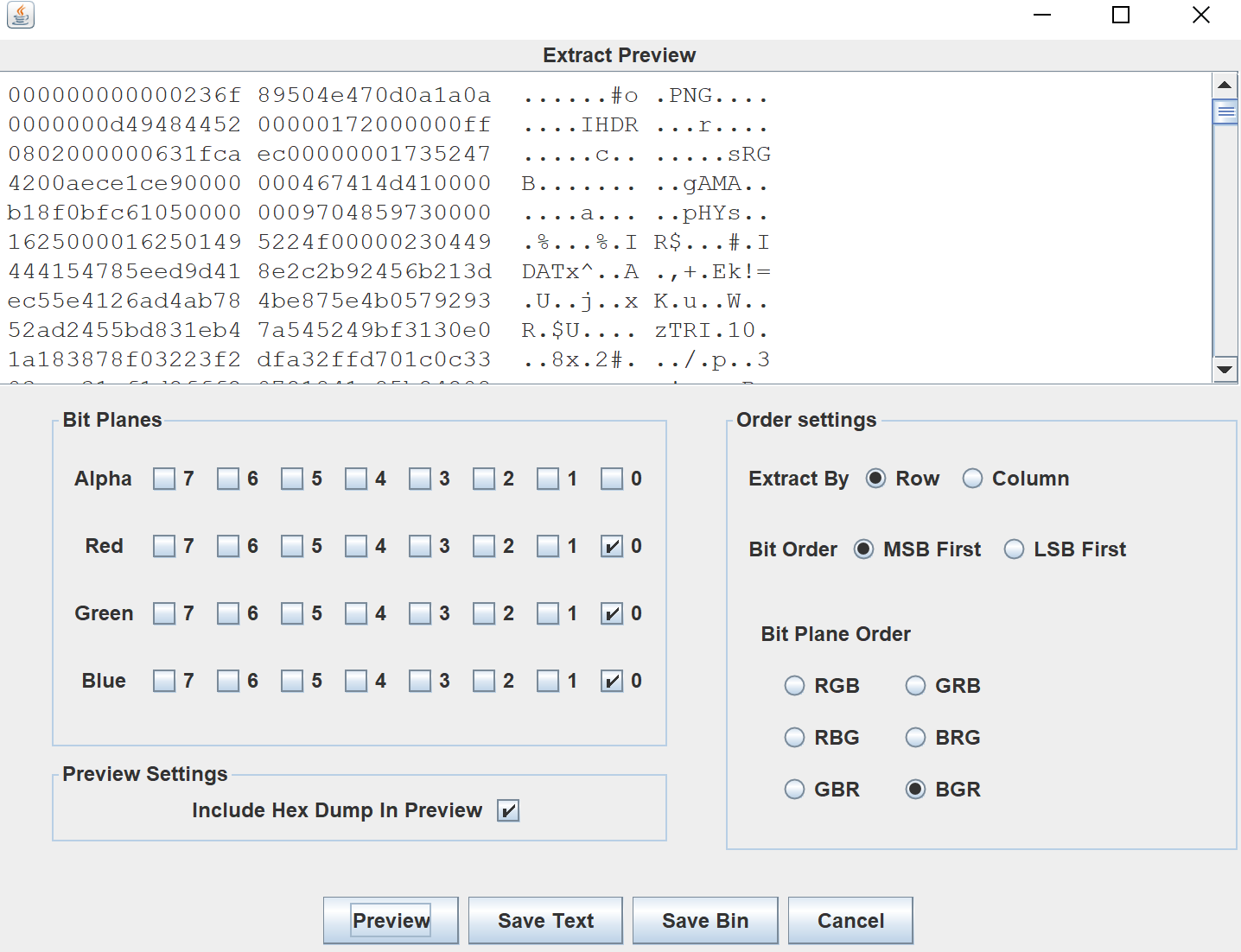
PNG文件头:
|
|
对照文件头,把前面几个字节去掉,打开看到:
猜密码为zhazhahui,解压flag.zip,得到:
|
|
栅栏n=13 fhvmy{Tk3_r0n_f7_8kh4axk?}
凯撒rot7 moctf{Ar3_y0u_m7_8ro4her?}
Hacker!!!
感谢@Sakura师傅和Sakura师傅的学弟
参考这篇博文
- 导出http对象
- 分析盲注
- 长度1326为正确
|
|
|
|
flag:moctf{Http_1s_d4ng3rI0u5}
李华的诱惑
解压看到password.txt,看着像像素值
Sublime打开,一共22500行,150 * 150试试
Python借助PIL还原,搜到的一个脚本,修改后如下:
|
|
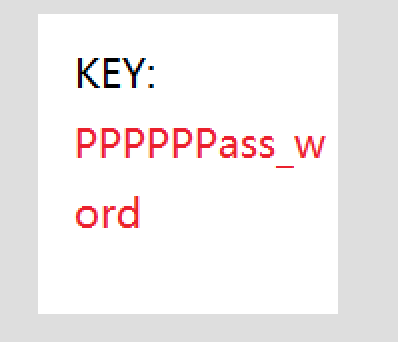
zip压缩包密码为PPPPPPass_word
|
|
直接解AES,flag:
|
|
签到
签到
moctf{500000000}

