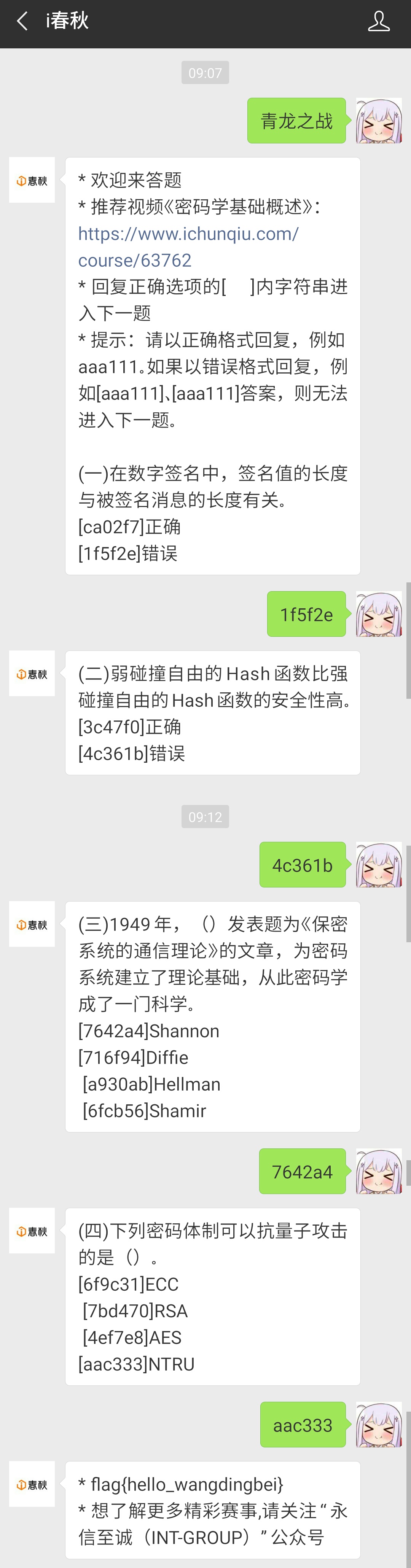
Misc 签到
flag{hello_wangdingbei}
Misc clip
010editor打开,搜IHDR有俩png文件,提取出来补好文件头
观察到最上面是明显的flag的样子,但是缺少下半部分
修改高度什么的貌似不好使,再仔细看,似乎是被拆分后重新拼的
于是画图打开(PS和美图秀秀都打不开),按着水平方向的边界拆成一个个单个的,然后再拼一起
拼完就能读出flag了
flag{0b008070-eb72-4b99-abed-092075d72a40}
Misc minified
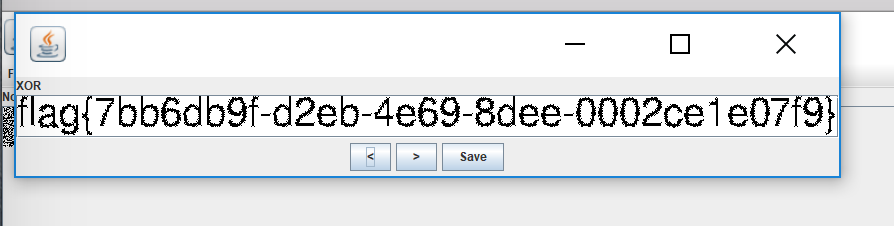
图片隐写,stego打开
red0通道全0,所以所有0通道都试一下吧
最后发现:
alpha0另存为一张图片,green0另存为一张图片
然后stego的combiner:
flag{7bb6db9f-d2eb-4e69-8dee-0002ce1e07f9}
Reverse Beijing
file一下,32位ELF,运行一下,输出一堆乱码
IDA打开,找到main函数,F5
发现21次重复过程:
每次传进去一个值到函数里,然后%c打印出来
点进函数,一堆case然后异或^
然后就琢磨呗
最后发现,是取每次case的、a^b的、b地址处的值,十六进制解ASCII码,得到flag(部分的case还要动态调orz
最后 flag{amazing_beijing}
Reverse advance
原题
wp
https://github.com/ctfs/write-ups-2016/tree/master/csaw-ctf-2016-quals/reverse/deedeedee-150
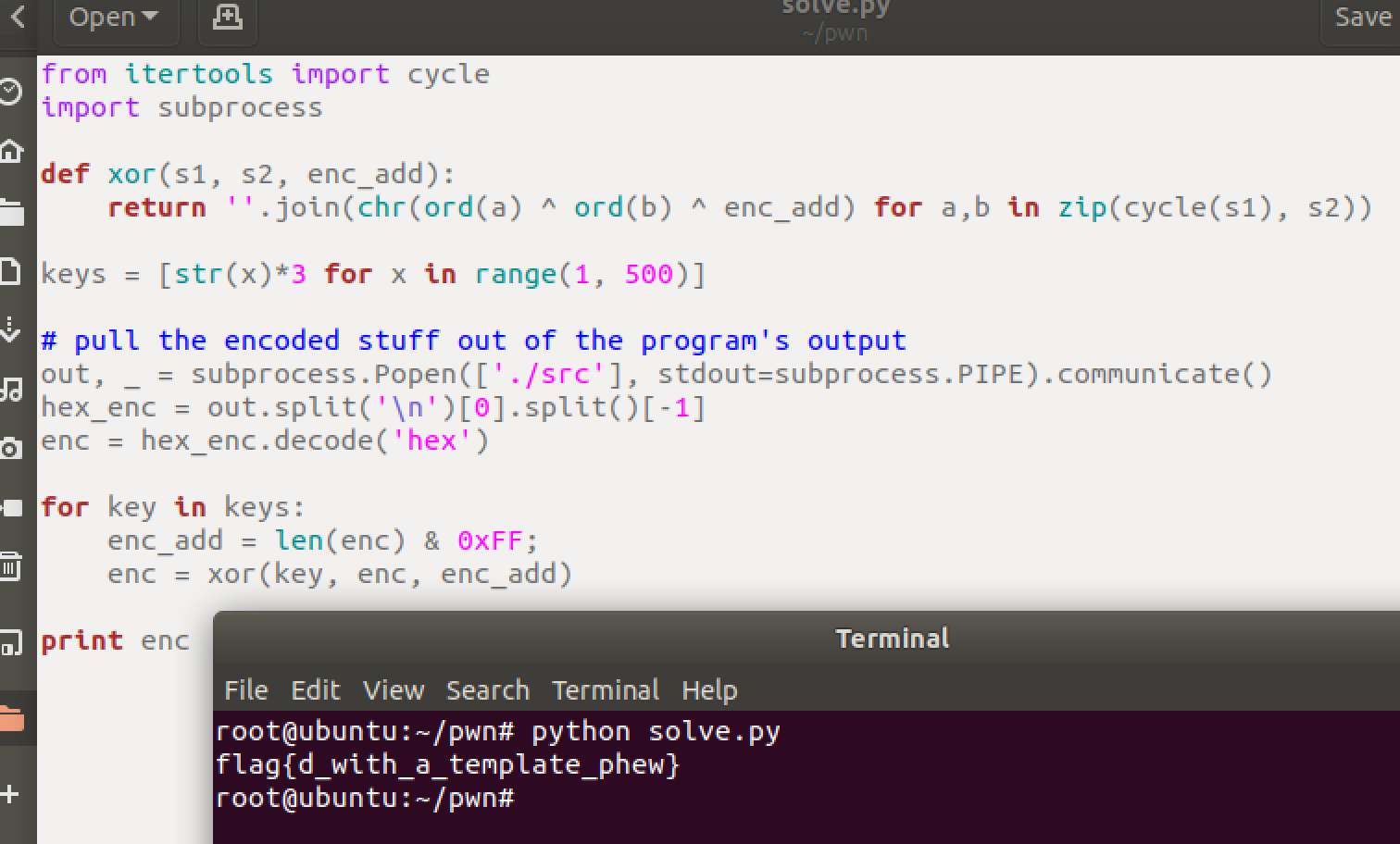
改个文件名就能直接跑= =
|
|
flag{d_with_a_template_phew}
Reverse blend
原题= =
照着wp怼
https://github.com/TechSecCTF/writeups/blob/master/CSAWQuals2017/realism/README.md
script:
|
|
output:
|
|
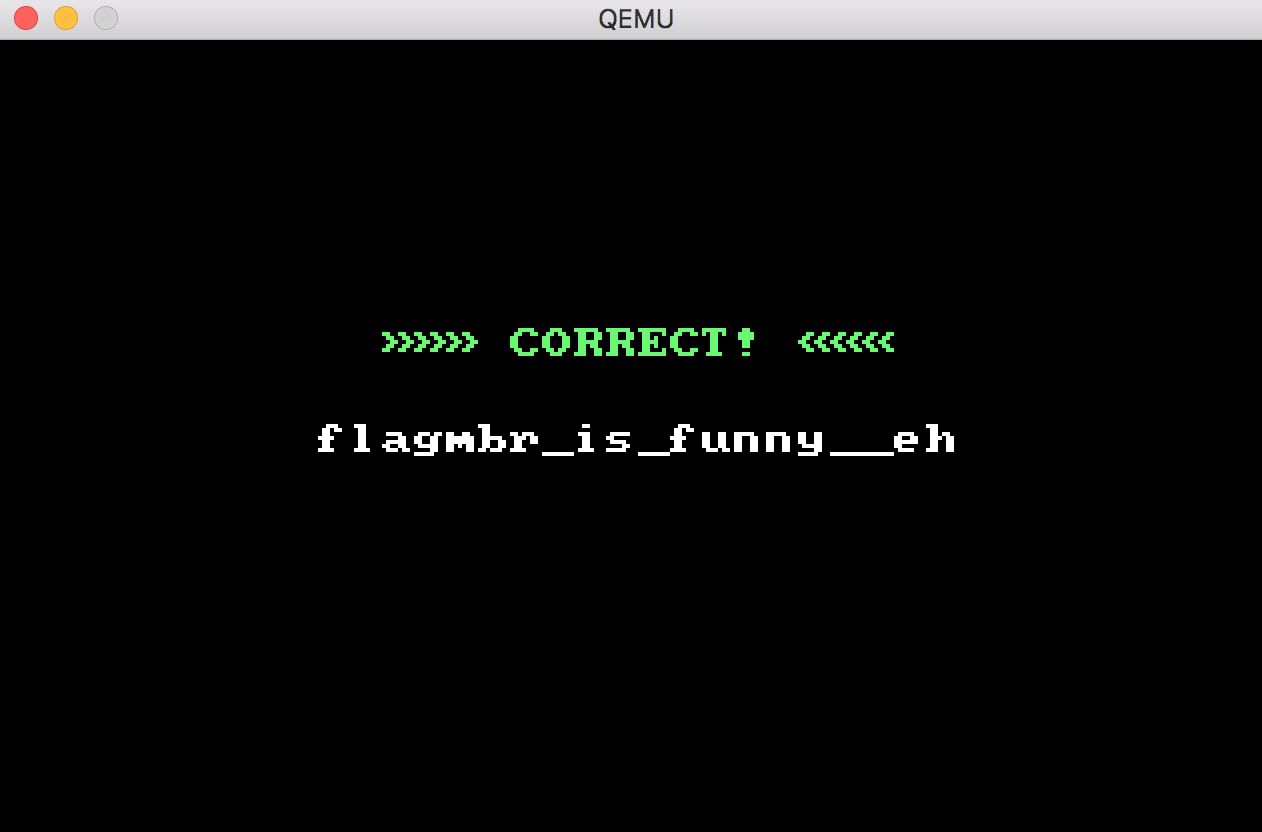
然后输出的部分代入到下面s.add()的部分,就解出来了,然后拼一下,代入到qemu中,正确
最终flag flag{mbr_is_funny__eh}